Summary
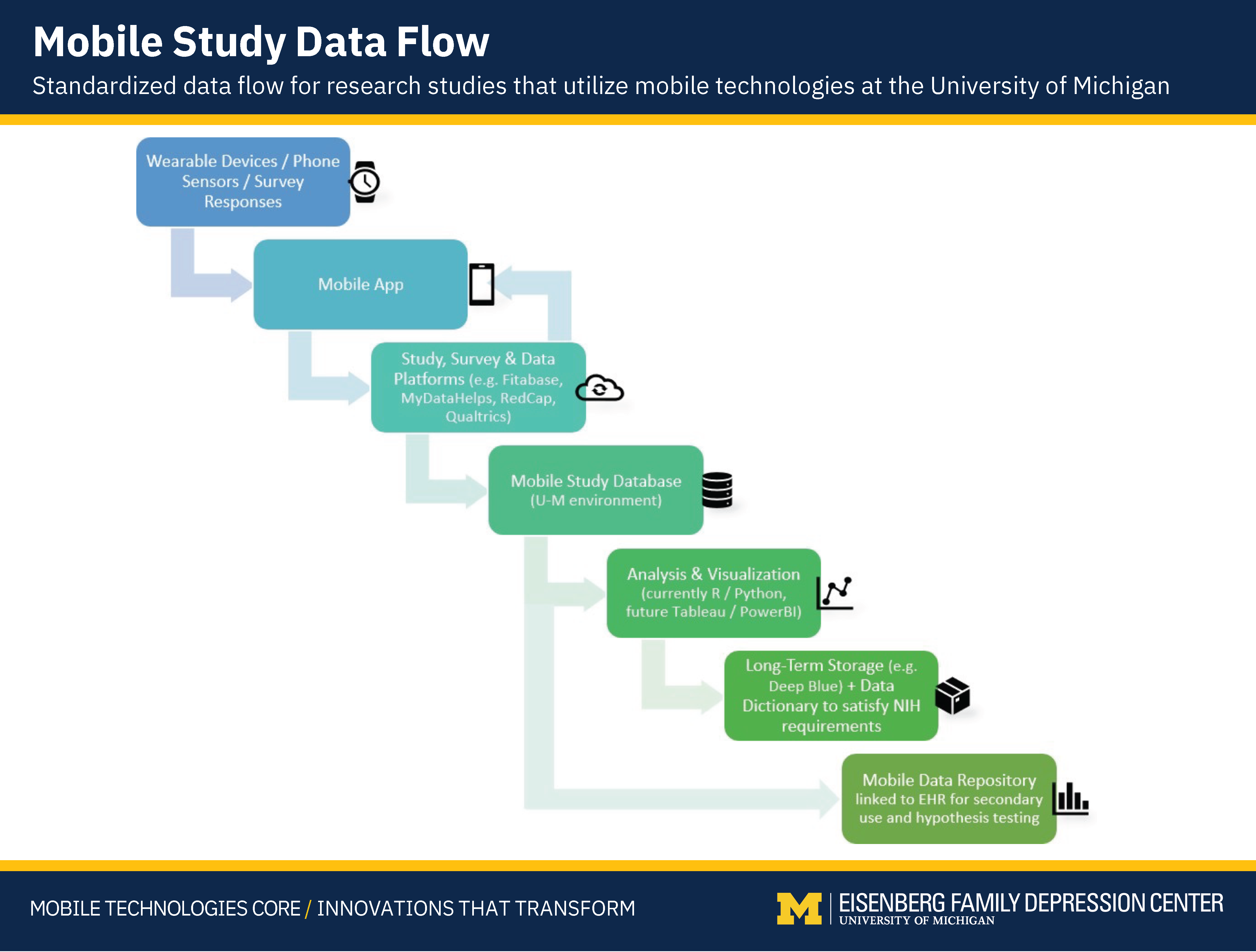
This is a Standardized data flow for research studies that utilize mobile technologies at the University of Michigan. It depicts how data typically moves from a smart watch or wearable device, into University resources behind a firewall, and finally lands on long-term storage for preservation and analytics.
Details
Integrating consumer wearable and nearable devices into a research study requires planning for scalability, storage, data analysis, and long-term data preservation. This data flow offers a visual guide of how data typically moves from a consumer's smart watch into a research database, and the different touch-points and system types required along the way. This data flow aims to standarize how mobile data flows at University of Michigan in an enterprise-ready, scalable and flexible manner.
Download Image | View as PDF
The Need for Standardization
Mobile data does not typically go straight from a smartwatch into the researchers' hands. Although researchers could access data programmatically from a device manufacturer's API, this would not be a scalable solution for hundreds or thousands of participants due to participant enrollment challenges, manual work, and lack of automated data syncing. Moreover, the large amounts of sensor and activity data generated by wearables means flat-file storage would severely limit analysis speed while presenting storage size and compliance challenges. Utilizing enterprise-grade databases, which are designed to handle large amounts of data, make syncing, analysis, modeling, visualizations and dashboards easier, thus allowing researchers to focus on the science rather than the technology. Finally, NIH requirements for long-term data storage and preservation present unique challenges, not just in terms of cost but also documentation of code and data that is more easily done through automated systems.
While established researchers may already have access to enterprise solutions for mobile data, junior and associate faculty and undergrad researchers may not have access to the IT infrastructure and technical expertise needed to successfully run a study with mobile data. The Mobile Technologies Core's mission is to make enterprise-grade infrastructure available to all U-M researchers, even when they are new to mobile tech or have no internal IT teams. Thus, standard data pipelines, common data models, analytics templates and common infrastructure are necessary to elevate mobile tech research at all levels, without requiring teams to re-invent everything. This standard data flow is the starting point for standardization.
Notes
Resources
- To learn more about how to integrate mobile data and mental health measures into your research, request a consultation from the Mobile Technologies Core.
About the Author
 |
Gabriel Mongefranco is a Mobile Data Architect at the University of Michigan Eisenberg Family Depression Center. Gabriel has over a decade of experience in data analytics, dashboard design, automation, back end software development, database design, middleware and API architecture, and technical writing.
| |
|